Contact Us
Thank you for your interest in our marketing agency services and all-in-one sales and marketing software Stand Out From The Pack. We are excited to hear from you and answer any questions you may have. To get in touch with us, please complete the enquiry form below and we will get back to you as soon as possible.
Security and Compliance Overview
(Last updated Dec 2024)
Introduction
Our Company and Products
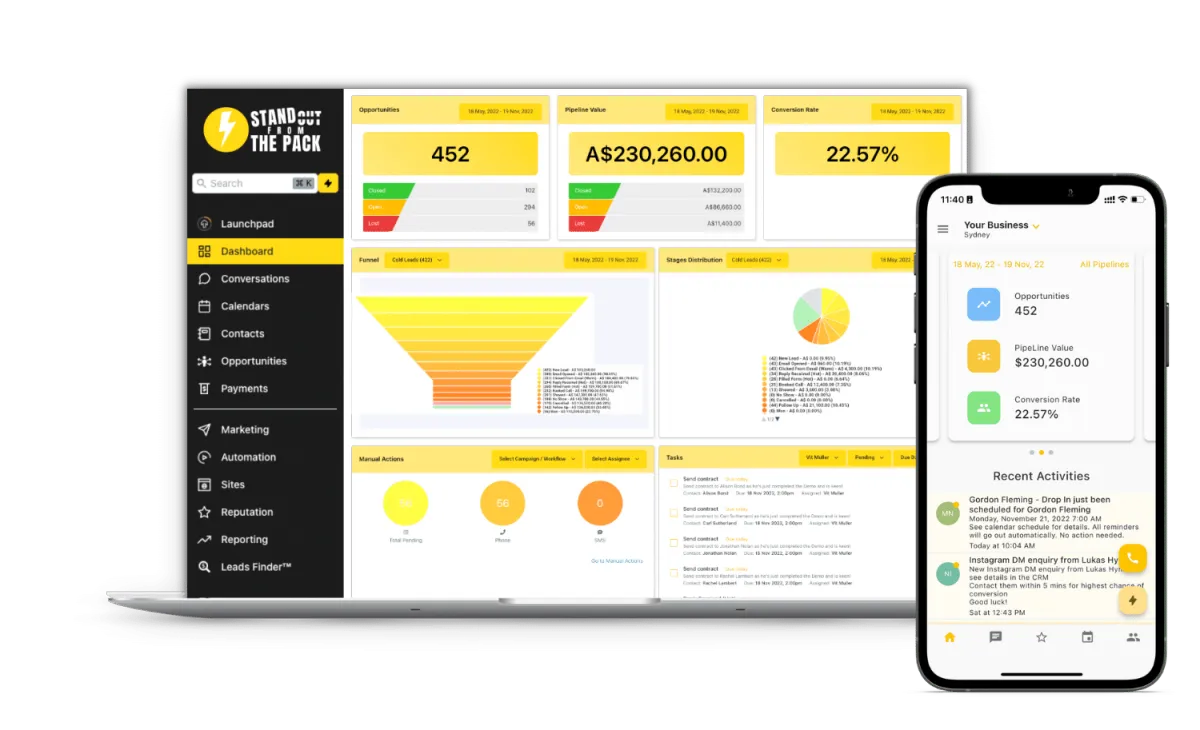
Developed with small business in mind, Stand Out From The Pack™'s goal is to help companies reach and surpass their marketing and sales goals. We believe in enhancing automation, improving communication, and boosting scalability in a consumer-friendly way, and we consistently provide future-embracing updates that exemplify these priorities.Since its inception, Stand Out From The Pack™ has continuously grown, increasing the impact created on the tech community and the SaaS industry. At Stand Out From The Pack™, we measure our success by the successes of our customers and therefore prioritize optimizing our offerings in order to meet their needs.Our AI-powered all-in-one sales, marketing, and customer relationship management (CRM) platform offers numerous features that are essential to sales and marketing teams of small businesses. This expansive software solution provides limitless opportunities for our customers to achieve their sales goals while being supported by our team of experts.
Stand Out From The Pack™ Security and Risk Focus
Stand Out From The Pack™’s primary security focus is to safeguard our customers’ data. Stand Out From The Pack™ has invested in the appropriate controls to protect and service our customers. This investment includes the implementation of dedicated corporate, product, and infrastructure security programs. Our Legal Team, in partnership with other departments, oversees the implementation of these programs.
Our Security and Compliance Objectives
We have developed our security framework using best practices for the SaaS industry. Our key objectives include:
Customer Trust and Protection: deliver superior products and services while protecting the privacy and confidentiality of dataAvailability and Continuity of Service: ensure availability of the service and minimize risks to service continuityInformation and Service Integrity: make sure that customer information is never corrupted or altered inappropriatelyCompliance with Standards: aim to comply with or exceed industry standard best practices.
Stand Out From The Pack™ Security Controls
In order to protect the data that is entrusted to us, Stand Out From The Pack™ utilizes layers of administrative, technical, and physical security controls throughout our organization. The following sections describe a subset of our most frequently asked questions about control.
A. Infrastructure Security
a. Cloud Hosting Provider
Stand Out From The Pack™ does not host any product systems or data within its physical offices. Stand Out From The Pack™ outsources hosting of its product infrastructure to leading cloud infrastructure providers such as Google Cloud Platform Services and Amazon Web Services. Our product infrastructure resides in the United States. We place reliance on Google’s and AWS’s audited security and compliance programs for the efficacy of their physical, environmental, and infrastructure security controls. Google provides a monthly uptime percentage to customers of at least 99.5%. You can find more information about the controls, processes, and compliance measures implemented by Google on their publicly available Compliance Resource Center. AWS guarantees between 99.95% and 100% service reliability, ensuring redundancy to all power, network, and HVAC services. The business continuity and disaster recovery plans for the AWS services have been independently validated as part of their SOC 2 Type 2 report and ISO 27001 certification. AWS’s compliance documentation and audit reports are publicly available at the AWS Cloud Compliance Page and the AWS Artifacts Portal.
b. Network and Perimeter
The Stand Out From The Pack™ product infrastructure enforces multiple layers of filtering and inspection on all connections across our web application, logical firewalls, and security groups. Network-level access control lists are implemented to prevent unauthorized access to our internal product infrastructure and resources. By default, firewalls are configured to deny network connections that are not explicitly authorized. Changes to our network and perimeter systems are controlled by standard change control processes. Firewall rulesets are reviewed periodically to help ensure that only necessary connections are configured.
c. Configuration Management
Automation drives Stand Out From The Pack™’s ability to scale with our customers’ needs and rigorous configuration management is baked into our day-to-day infrastructure processing. The product infrastructure is a highly automated environment that expands capacity as needed. All server configurations are embedded in images and configuration files, which are used when new containers are provisioned. Each container includes its own hardened configuration and changes to the configuration and standard images are managed through a controlled change pipeline. Server instances are tightly controlled from provisioning through deprovisioning, ensuring that deviations from configuration baselines are detected and reverted at a predefined cadence. In the event that a production server deviates or drifts from the baseline configuration, it will be overwritten with the baseline within 30 minutes. Patch management is handled using automated configuration management tools or by removing server instances that are no longer compliant with the expected baseline.
d. Logging
Actions and events that occur within the Stand Out From The Pack™ application are consistently and comprehensively logged. These logs are indexed and stored in a central logging solution hosted in Stand Out From The Pack™’s cloud environment. Security relevant logs are also retained, indexed, and stored to facilitate investigation and response activities. The retention period of logs depends on the nature of the data logged. Write access to the storage service in which logs are stored is tightly controlled and limited to a small subset of engineers who require access.
e. Alerting and Monitoring
Stand Out From The Pack™ invests in automated monitoring, alerting, and response capabilities to continuously address potential issues. The Stand Out From The Pack™ product infrastructure is instrumented to alert engineers and administrators when anomalies occur. In particular, error rates, abuse scenarios, application attacks, and other anomalies trigger automatic responses or alerts to the appropriate teams for response, investigation, and correction. Many automated triggers are also designed to immediately respond to anomalous situations. For example, traffic throttling, process termination, and similar functions are triggered at predefined thresholds.
B. Application Security
a. Web Application Defenses
All customer content hosted on the platform is protected by firewall and application security. The monitoring tools actively monitor the application layer and can alert on malicious behavior based on behavior type and session rate. The rules used to detect and block malicious traffic are aligned to the best practice guidelines documented by the Open Web Application Security Project (OWASP), specifically the OWASP Top 10 and similar recommendations. Protections from Distributed Denial of Service (DDoS) attacks are also incorporated, helping to ensure customers’ web sites and other parts of the Stand Out From The Pack™ products are continuously available.
b. Development and Release Management
Stand Out From The Pack™ optimizes our products through a modern continuous delivery approach to software development. New code is regularly deployed. Code reviews, testing, and merge approval is performed before deployment. Static code analysis runs regularly against code repositories and blocks known misconfigurations from entering the code base. Approval is controlled by designated repository owners and once approved, code is automatically submitted to Stand Out From The Pack™’s continuous integration environment where compilation, packaging and unit testing occur. Dynamic testing for security vulnerabilities is performed periodically against our applications. Newly developed code is first deployed to a dedicated and separate QA environment for the last stage of testing before being promoted to production. Network-level and project-level segmentation prevents unauthorized access between QA and production environments. All code deployments are automated and in case of failures, the changes can be reverted. The deploying team manages notifications regarding the health of their applications and if a failure occurs, rollback processes are immediately engaged. We use extensive software gating and traffic management to control features based on customer preferences (private beta, public beta, full launch). Stand Out From The Pack™ features seamless updates and, as a SaaS application, there is no downtime associated with releases. Major feature changes are communicated through in-app messages and/or product update posts.
c. Vulnerability Management
The Stand Out From The Pack™ team manages a multi-layered approach to vulnerability management, using a variety of industry-recognized tools and threat feeds to ensure comprehensive coverage of our technology stack. Vulnerability scans are configured to scan for vulnerabilities on a regular basis, using adaptive scanning inclusion lists for asset discovery as well as the latest vulnerability detection signatures. We perform annual penetration tests against our applications and infrastructures to identify vulnerabilities that may present security related risks. Relevant findings are assessed, and mitigations are prioritized accordingly.
C. Customer Data Protection
a. Data Classification
Per the Stand Out From The Pack™’s Terms of Service, our customers are responsible for ensuring they only capture appropriate information to support their marketing, sales, services, content management, and operations processes. The Stand Out From The Pack™ products should not be used to collect or store sensitive information, such as credit or debit card numbers, financial account information, Social Security numbers, passport numbers, financial or health information except as otherwise permitted.
b. Tenant Separation
Stand Out From The Pack™ provides a multi-tenant SaaS solution where customer data is logically separated using unique IDs to associate data and objects to specific customers. Authorization rules are incorporated into the design architecture and validated on a continuous basis. Additionally, we log application authentication and associated changes, application availability, and user access and changes are logged.
c. Encryption
All data is encrypted in transit with TLS version 1.2, or 1.3 and 2,048 bit keys or better. Transport layer security (TLS) is also a default for customers who host their websites on the Stand Out From The Pack™ platform. Stand Out From The Pack™ leverages several technologies to ensure stored data is encrypted at rest. Platform data is stored using AES-256 encryption. User passwords are hashed following industry best practices, and are encrypted at rest.
d. Key Management
Encryption keys for both in transit and at rest encryption are securely managed by the Stand Out From The Pack™ platform. TLS private keys for in transit encryption are managed through our content delivery partner. Volume and field level encryption keys for at rest encryption are stored in a hardened Key Management System (KMS). Keys are rotated at varying frequencies, depending upon the sensitivity of the data they govern. In general, TLS certificates are renewed annually. Stand Out From The Pack™ is unable to use customer supplied encryption keys at this time.
D. Data Backup and Disaster Recovery
a. System Reliability and Recovery
Stand Out From The Pack™ is committed to minimizing system downtime. All Stand Out From The Pack™ product services are built with redundancy. Server infrastructure is strategically distributed across multiple distinct availability zones and virtual private cloud networks within our infrastructure providers, and all web, application, and database components are deployed with a point in time recovery.
b. Back up Strategy
i. System Backups
Systems are backed up on a regular basis with established schedules and frequencies. Seven days’ worth of backups are kept for any database in a way that ensures restoration can occur easily. Backups are monitored for successful execution, and alerts are generated in the event of any exceptions. Failure alerts are escalated, investigated, and resolved. Data is backed up daily to the local region. Monitoring and alerting is in place for replication failures and triaged accordingly.
ii. Physical Backup Storage
Because we leverage public cloud services for hosting, backup, and recovery, Stand Out From The Pack™ does not implement physical infrastructure or physical storage media within its products. Stand Out From The Pack™ does not generally produce or use other kinds of hard copy media (e.g., paper, tape, etc.) as part of making our products available to our customers.
iii. Backup Protections
By default, all backups are protected through access control restrictions and write once read many (WORM) protections on Stand Out From The Pack™ product infrastructure networks, and access control lists on the file systems storing the backup files.
iv. Customer Data Backup Restoration
Stand Out From The Pack™ customers don't have access to the product infrastructure in a way that would allow a customer-driven failover event. Disaster recovery and resiliency operations are managed by Stand Out From The Pack™ product engineering teams. In some cases, customers can use the recycle bin to directly recover and restore contacts, opportunities, custom fields, custom values, tags, notes, and tasks up to 30 days after they were deleted. Changes to web pages, blog posts, or emails can be restored to previous versions of content using version history. For customers who wish to additionally back up their data, the Stand Out From The Pack™ platform provides many ways of ensuring that you have what you need. Many of the features within your Stand Out From The Pack™ portal contain export options, and the Stand Out From The Pack™ library of public APIs can be used to synchronize your data with other systems.
c. Identity and Access Control
i. Product User Management
The Stand Out From The Pack™ products allow for granular authorization rules. Customers are empowered to create and manage the users in their portals, assign the privileges that are appropriate, and limit access as they see fit.
ii. Product Login Protections
The Stand Out From The Pack™ products allow users to login to their Stand Out From The Pack™ accounts using the native Stand Out From The Pack™ login. The native login enforces a uniform password policy which requires a minimum of 8 characters and a combination of lower and upper case letters, special characters,, and numbers. People who use Stand Out From The Pack™’s native login cannot change the default password policy. Customers who use Stand Out From The Pack™’s built-in login are protected by two-factor authentication for their Stand Out From The Pack™ accounts. Portal administrators may require all users to have two-factor authentication enabled.
iii. Stand Out From The Pack™ Employee Access to Customer Data
1. Access to Production Infrastructure
User access to internal data stores and production infrastructure is strictly controlled. Stand Out From The Pack™ employees are granted access using a role-based access control (RBAC) model. Day to day access is minimized to members of the Engineering team and persistent administrative access is restricted. Additionally, direct network connections to product infrastructure devices over SSH or similar protocols is prohibited, and engineers are required to authenticate first through a bastion host or "jump box" or have assigned IAM role to the resource before accessing server environments.
2. Access to Customer Portals
By default, Customer Support, Services, and other customer engagement staff can obtain limited access to parts of your Stand Out From The Pack™ account to help you with using Stand Out From The Pack™. The Stand Out From The Pack™ application also uses a JITA model to grant employees access to a customer’s portal for a limited duration (Portal JITA). Each Portal JITA request is logged. Access is tied to a specific customer’s portal for a maximum 24-hour period. Stand Out From The Pack™ also utilizes risk-based monitoring to detect unusual Portal JITA activity. When accessing a portal using Portal JITA, Stand Out From The Pack™ account owners are unable to perform high-risk actions such as:
Changing domain or SSO settingsExporting users/contactsViewing/creating/deleting/rotating private app keysImporting data to the CRMDeleting contacts, companies, deals, and tickets
User logins, Stand Out From The Pack™ employee access, security activity, and content activity is logged.
iv. Corporate Authentication and Authorization
Access to the Stand Out From The Pack™ company network requires MFA. Password policies follow industry best practices for required length, complexity, and rotation frequency. Password vaults are in place to manage certain administrative account passwords, and access to the vault is managed through Role Based Access Control or through the JITA process. We have built an extensive support system to streamline and automate our security management and compliance activities.In addition to many other functions, we ensure that permission grants are appropriate, employee events are managed, access revocations are timely, change logs are effectively collected, and compliance evidence is preserved. Employee access and permissions to key internal systems are manually reviewed semi-annually to help ensure access granted is necessary for their job function.
d. Organizational and Corporate Security
i. Background Checks and Onboarding
Stand Out From The Pack™ employees undergo a third party background check prior to formal employment offers. Reference verification is performed at the hiring manager's discretion. Upon hire, all employees must read and acknowledge Stand Out From The Pack™’s Employee Handbook and Code of Conduct which help to define employee's security responsibilities in protecting company assets and data.
ii. Policy Management
To help keep all our employees on the same page with regard to protecting data, Stand Out From The Pack™ documents and maintains written policies and procedures. Specifically, Stand Out From The Pack™ maintains a core Written Information Security Policy, which covers a variety of topics such as data handling requirements, privacy considerations, and disciplinary actions for policy violations. Policies are reviewed and approved at least annually.
iii. Security Awareness Training
Stand Out From The Pack™ employees are required to complete CyberSafety training when they start their employment, and training is made available annually thereafter. The CyberSafety training also includes phishing awareness.
iv. Vendor Management
Stand Out From The Pack™ may leverage third party service providers to support the development of our product as well as internal operations. We ensure that our vendors have appropriate security and privacy controls in place as part of our contractual relationship with them. We also maintain a list of our sub-processors (which may change from time-to-time) within our Data Processing Agreement.
v. Endpoint Protection
Company issued laptops are centrally managed and are configured to maintain full disk encryption. We implement a Mobile Device Management solution that provides a centralized platform for IT administrators to manage and monitor mobile devices in an organization. This includes configuring device settings, enforcing security policies, deploying apps, and ensuring compliance with corporate policies.
e. Compliance
i. Sensitive Data Processing and Storing
Please see our Terms of Service and Privacy Policy for additional information on how and why we process data. Please note that, while Stand Out From The Pack™ customers may pay for services by credit card, Stand Out From The Pack™ does not store, process, or collect credit card information submitted to us by customers, and we are not PCI-DSS compliant. We leverage PCI-compliant payment card processors to ensure that our payment transactions are handled securely.
f. Privacy
As described in our Privacy Policy, we do not sell your personal data to third parties. The protections described in this document and other protections that we have implemented are designed to ensure that your data stays private and unaltered.
i. Data Retention and Data Deletion
Customer data is retained for as long as you remain an active customer. Current and former customers can make written requests to have certain data deleted, and Stand Out From The Pack™ will fulfill those requests as required by privacy rules and regulations. Stand Out From The Pack™ retains certain data like logs and related metadata in order to address security, compliance, or statutory needs. Stand Out From The Pack™ does not currently provide customers with the ability to define custom data retention policies.
ii. Privacy Program Management
Stand Out From The Pack™’s Legal Team collaborates with our engineering and product development teams to implement an effective privacy program. Information about our commitment to the privacy of your data is described in greater detail in our Privacy Policy and Data Processing Agreement.
iii. Breach Response
Stand Out From The Pack™ will notify customers as required by law if it becomes aware of a data breach that impacts your personal data.
g. GDPR
Stand Out From The Pack™ aims to provide features that enable our customers to easily achieve and maintain their GDPR compliance requirements. Please refer to our GDPR page for more information. While Stand Out From The Pack™ seeks to enable your GDPR compliance efforts, use of the Stand Out From The Pack™ product alone does not make you GDPR compliant.
h. Document Scope and Use
This document is intended to be a resource for our customers. It is not intended to create a binding or contractual obligation between Stand Out From The Pack™ and any parties, or to amend, alter or revise any existing agreements between the parties. Stand Out From The Pack™ is continuously improving the protections that we have implemented, so our procedures may be subject to change.
i. Contact Us
Questions about this document? We want to hear from you! You can reach as at [email protected].
S.W.A.S.
/swɒs/
(Software with a service)
We're a digital marketing agency with SWAS. We have a strong focus on generating more sales opportunities through effective marketing strategies and state-of-the-art software.
We’ve Got You Covered
Lead Generation
Social media Ads, Google ads or totally free lead gen strategies; we have the tried & proven know-how to get you qualified leads that convert.

Social Media Management
Managing your socials doesn't have to be overwhelming. Save time on scheduling content and responding to comments and messages.
Content Creation
Whether you need blog posts, website copy, or social media updates, we can help you stand out from the pack and attract more customers.
Sales Funnels
We specialise in creating a custom funnels that fits your unique needs and helps you convert more leads into customers.
Reputation Management
With our Review Request System™, we can help you build a positive online presence and ensure that your customers see you as the best option.

SMS Marketing
Incredibly effective way to reach new customers, increase loyalty among current customers, and drive more sales at low cost. When done right.
Website Development
We'll work with you to create a website that reflects your unique brand and that will help you stand out from the competition.
Email Marketing
We'll help you create eye-catching emails that will grab your readers' attention, and turn it into action in form of more replies and sales.

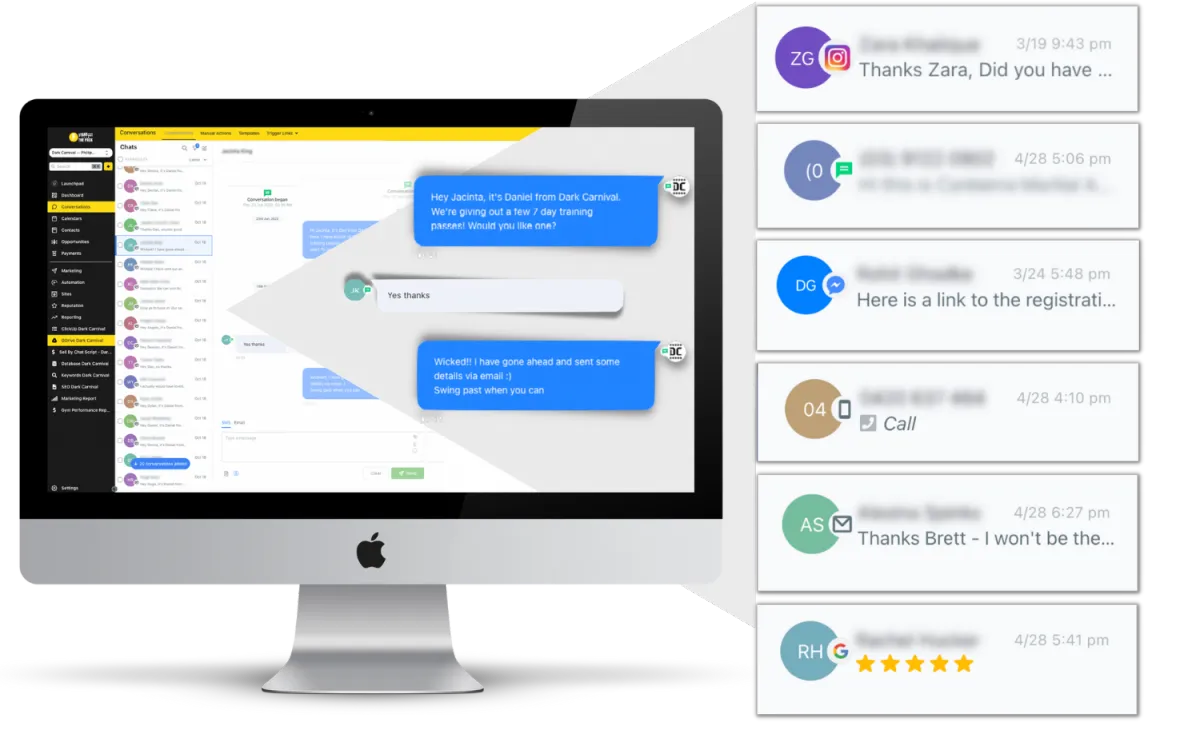
We Make it Easy to Connect With All Your Leads
Never worry about losing potential leads or customers again! With our Omni-Channel Chat™, you can connect with them through texting, live chat, bulk messaging, Google My Business, Instagram and Facebook messages – all in one inbox. This way, you'll never miss another chance to make a connection.
Recent Projects Empowering Your Business Growth
Transforming Ideas into Success Stories Through Strategic Partnerships
At Stand Out From The Pack™, we don't just provide software; we're your strategic partner in growth. Our team is dedicated to delivering tailored marketing campaigns and website development to drive your business success.
Here are a few examples of our recent work:
Website Design & Development
Sales Funnel Development and Lead Generation
Retargeting Campaigns on Facebook and Instagram
Email and SMS Lead Qualifying Campaigns
Success Stories


Wonderful experience working with Vit, he knows how to make a big impact in your business and helps to create real change. Brilliant!
Daniel Murray
Speaker | Leadership Trainer | Strategic Advisor at Empathic Consulting


Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.
Tom Adam
Chief Instructor / Founder at Canberra Martial Arts & Fitness


Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Lorem ipsum dolor sit amet, consectetur adipiscing elit.
Tony Lane
Director - Registered Liquidator at Beacon Advisory
Ready To Level Up Your Sales & Marketing?
Helping businesses capture, nurture and close more leads since 2017
🚀 We are Stand Out From The Pack™. We're a digital marketing agency with an automated sales and marketing system as a service. We help small and medium size businesses capture, nurture and close more leads and increase profits at the same time. We strongly focus on generating more sales opportunities through effective marketing strategies and our state-of-the-art software powered by smart automations and AI. 🔥
@ Copyright 2026 - VITFIT Pty Ltd t/a Stand Out From The Pack™ | ABN 31 602 151 842
Made with ♥ In Canberra, Australia



